Department of Computer Science at Cihan University – Duhok, held an international online workshop on the Google Meet platform entitled “Database Security and Authentication”.
🎙️Hosted by the speaker:
📌 Dr. Bazeer Ahamed: Lecturer in the Department of Information Technology University of Technology And Applied Sciences Al Musanna Sultanate of Oman
🎙️Session Moderator
📌Mr. Bilal Hikmat Rasheed: Head of Computer Science Department Cihan University – Duhok.
Talk about:
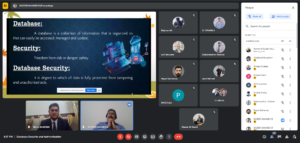
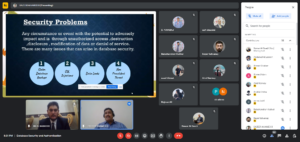
Database security refers to the range of tools, controls, and measures designed to establish and preserve database confidentiality, integrity, and availability. This article will focus primarily on confidentiality since it’s the element that’s compromised in most data breaches.
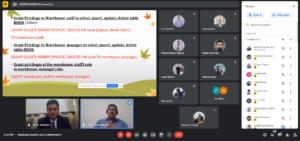
Windows authentication requires a user to first authenticate to Windows with their login and password. Once a user has been authenticated to Windows, they can then connect to SQL Server using Windows authentication. That is, provided their Windows account has been granted access to SQL Server via a login (more on logins later). Windows authentication is tightly coupled with Windows Security and is also known as Integrated Security. Windows authentication works great when a person is part of a Windows domain.
At the end of the session, many questions and scientific interventions were raised by attendance.